Blockchain 101 – Part 4: Distributed P2P Networks
Part 3: The Immutable Ledger
Finally, I found the time to continue the Blockchain 101 serie. Unfortunately this last few months have been really really busy...I am very sorry for that.
However, in order to make up with you guys today I am going to discuss a very very interesting topic: the concept of Distributed P2P Networks.
As anticipated in Part 3, the concept of immutable ledger mixed with the concept of distributed P2P networks allows to build secure and decentralized Blockchains.
But how does this work?
In the previous part we discussed how a blockchain can protect data inside the blocks through the concept of immutability, making it hard for an attacker to alter records in the blocks without invalidating all the remaining blocks.
Limitations of a Centralized Blockchain System
However, with a centrally stored blockchain, nobody could hinder a highly determined attacker from altering a block and modifying all the following ones. After all, the chain would still be valid.
As a matter of fact, if you succeeded in changing the records in a block and recomputing the hashes, that would cause a "realignment" of all the block hashes still keeping the blockchain valid.
![]()
Furthermore, what would happen if a block in the chain got altered as a result of an unknown error? How could we restore the previous data from a failure?
These are the problem which Distributed P2P Networks aim to solve.
(NOTE: if you feel like you are missing something here please stop reading: I vividly suggest you to go back and read the previous parts as they lay the foundation for this part and the following ones).
Distributed P2P Networks
A distributed Peer-To-Peer (P2P) network has many many nodes (or computers) which are all interconnected together. So imagine a worldwide network of interconnected computers. Ideally, all computers could be interconnected to each other (fully-connected network) but that is not always the case. Sometimes two very distant nodes are less connected with respect to nodes which are "nearer" distance wise.
So, how can we exploit this simple concept of P2P networks to further secure our blockchain system? The main idea is to have an exact copy of the chain on every node in the network (could be thousands or even millions of computers depending on how big the network is). A node in the network could be a server, a laptop or a desktop computer. Each node interconnect with each other in an anonymous way using cryptography and, at the same time, stores a copy of the entire blockchain.
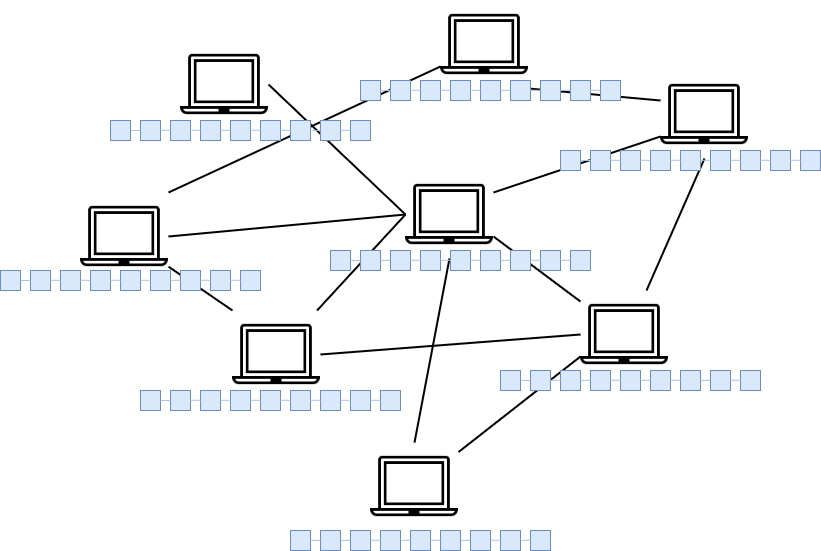
"Ok, great. But how does this mix between distributed networks and the blockchain can create a more secure system?"
Let's demonstrate this by introducing an example: each time a new block is added to the blockchain by a node, the new addition is propagated across the entire network in order to let the other nodes update their local copy of the blockchain. So the new block is propagated throughout the network until all the nodes are updated.


This basically means that all the nodes of the network have the same copy of all the records (or transactions) stored in the blocks all the time.
So as time passes by, new blocks are added to the chain.
Following up with our example, let's suppose that, as in the previous example discussed in Part 3, an hacking attempt occurs on a local blockchain copy of a single node (we will call it node A). An attacker try to maliciously modify a block where some money transactions are stored. The tampered block of course would cause the invalidation of entire local copy of the chain hosted on node A. All the blocks after the modified one, are now invalid.
Let's further hypothesize that the attacker is able to go through all the invalid nodes and recompute the hashes in order to make the entire local copy of the blockchain valid again.
This is where the distributed network plays a crucial part...
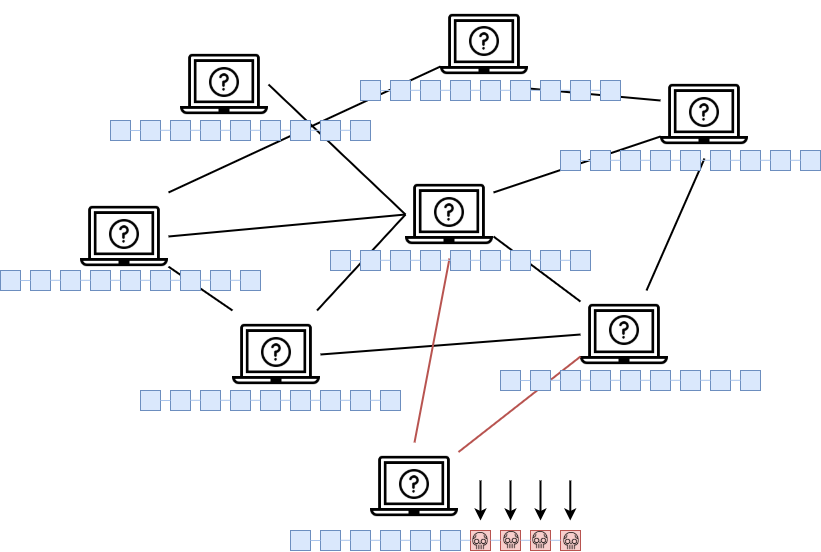
Consensus
In the example discussed in Part 3, since the blockchain was stored on a single machine, and not across a distributed network, the hacking attempt would have been successful. With a P2P network instead, the attempt would fail. This is because the network is constantly up to date and every node share the exact same copy of the chain. This means that the network has a protocol for constantly checking that all the peers have the same exact copy of the blockchain.
So each node's locally stored chain must match with the other local copies in the network. The peers which are "adjacent" to the hacked one (node A), would immediately realize that the chain stored on the compromised node is invalid and they would signal that to the compromised node.
Let me pause for a while...
We are in presence of a key concept here: how's that the nodes in the network instantly signal that the compromised computer has an invalid chain?
This happens through a "democratic" process.
The Majority of the nodes would realize that the invalid chain resides only on the minority of the nodes (in our example only 1, which is node A).
So this basically means that the network must reach a CONSENSUS on which chain is valid every time a new block is added in a local chain of a single node. This is how we bring trust into a trustless environment such as an anonymous distributed P2P network.
And let me tell you, this is fascinating! How a technology design is capable of bringing trust through a simple but effective consensus mechanism.
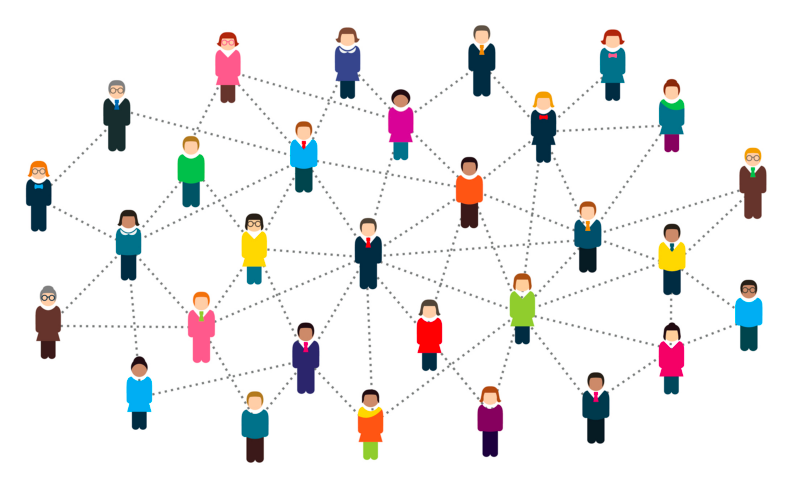
So the other nodes would then signal the problem to the compromised node, forcing him to replace its current local chain with the correct one which is stored on the majority of the peers in the network. This time the attacker cannot attack a single computer, as in the example in Part 3. The attacker would have to compromised the majority of the nodes in the network at the same time (in particular, more than a half of the network nodes).
This is also known as the 51% Attack. More info about this can be found here.
Wrapping up
Thanks to P2P networks and consensus we can now further secure our blockchain system.
So just to recap, we started with a simple chain of blocks which stored records and we gradually added more security levels on top of it, one after another such as: hash, cryptography, p2p network and consensus.
If you still have questions do not hesitate in contacting me using my email address (you can find it in the footer of the website) or via the contact page.
Also, you can hit me up on Twitter.
If you enjoyed my content, please share!
Suggested reading: https://medium.com/@VitalikButerin/the-meaning-of-decentralization-a0c92b76a274

